In a world where cyber attacks are on the rise, with an increase of 57%[1] in reported breaches among small to medium-sized businesses (SMBs), tackling cyber risk is critical. According to a report by Digital Ocean[1], one of the top concerns for organizations (Specifically SMBs) is the lack of time to manage security. Reducing the risks of cyber attacks time-efficiently is crucial; a robust cyber risk management program plays a significant role in ensuring businesses invest their time and resources in the right areas.
Cybersecurity risk management is a vital process that organizations undertake to safeguard their valuable assets in an interconnected world. It involves systematically identifying organizations’ assets, assessing vulnerabilities, and mitigating risks proactively and comprehensively. Cybersecurity risk management ensures the protection of critical information and infrastructure by evaluating vulnerabilities and potential threats, implementing adequate controls and safeguards, and continuously monitoring emerging threats. In this comprehensive guide, we will go over the main components of a solid risk management program, including how to adapt it for small and medium companies with limited resources.
Risk Management Process 📕
The risk management process comprises several vital steps organizations should follow to manage cybersecurity risks effectively. These steps include:
- Risk Identification: Identify and categorize the assets within the organization that are susceptible to cyber threats. Those assets include sensitive data, intellectual property, network infrastructure, and customer information.
- Risk Assessment: Evaluate and prioritize the identified risks based on their potential impact and likelihood of occurrence. This step involves assessing vulnerabilities, existing controls, and possible consequences of successful attacks.
- Risk Treatment: Develop a strategy to mitigate identified risks effectively. Risk treatment may involve implementing technical controls, conducting employee training and awareness programs, establishing incident response plans, and regularly updating software and systems.
- Risk Monitoring: Continuously monitor and review the effectiveness of implemented controls and safeguards. Regular audits, penetration testing, and threat intelligence analysis can help identify new vulnerabilities and emerging risks.
- Risk Response: In the event of a cyber-attack or security incident, organizations should have a well-defined response plan. This plan should outline the immediate actions, such as isolating affected systems, notifying relevant stakeholders, and initiating incident response procedures.
- Risk Communication: Effective communication is crucial throughout the risk management process. Organizations should ensure that stakeholders know the risks, mitigation strategies, and their roles and responsibilities in maintaining cybersecurity.
Categories Risk Treatment 🛠️
When it comes to risk treatment, organizations can choose from several options based on the nature of the risks and available resources. The main categories of risk treatment include:
- Risk Avoidance: This involves eliminating or avoiding activities that may pose high risks. It could include discontinuing certain business practices or not engaging in activities that expose the organization to significant cybersecurity threats.
- Risk Mitigation: Mitigating risks involves implementing controls and safeguards to reduce the likelihood or impact of potential cyber-attacks. Mitigations may include deploying firewalls, antivirus software, encryption mechanisms, access controls, and regular data backups.
- Risk Transfer: Organizations can transfer the risk to a third party through insurance or outsourcing certain cybersecurity functions.
- Risk Acceptance: Organizations may choose to accept certain risks if the cost of mitigation outweighs the potential impact. However, accepting risk should be based on thoroughly analyzing the risks and their possible consequences.
Risk Appetite and Risk Tolerance
Risk appetite and risk tolerance are two essential concepts in cybersecurity risk management.
- Risk Appetite: Risk appetite refers to an organization’s willingness to accept and tolerate risk. It is influenced by various factors, including business objectives, industry regulations, and the organization’s risk culture. Defining a clear risk appetite helps guide decision-making processes and ensures alignment with the organization’s goals.
- Risk Tolerance: Risk tolerance, on the other hand, represents the level of risk that an organization is willing to accept before taking corrective actions. It helps establish boundaries for acceptable risk levels and manages risks within predefined limits.
Risk appetite and tolerance should be defined as part of the risk management program to guide risk-related decisions and resource allocation.
Standards for Risk Management
Various standards and frameworks guide organizations in establishing effective cybersecurity risk management practices. Some of the widely recognized standards include:
- ISO 27001: ISO 27001 is an international information security management system (ISMS) standard. This standard provides a systematic approach to managing an organization’s information security risks.
- NIST Cybersecurity Framework: Developed by the National Institute of Standards and Technology (NIST), this framework provides a flexible and scalable approach to managing cybersecurity risks. It includes five core functions: Identify, Protect, Detect, Respond, and Recover.
Tips for Smaller Teams
Implementing comprehensive cybersecurity risk management practices can be challenging for small and medium-sized companies with limited resources. However, some strategies can help adapt the standards to the specific needs of smaller teams.
- Prioritization: Identify and prioritize the most critical assets and risks based on their potential impact. Focus on protecting the most valuable and sensitive information first. A good understanding of the business and the industry you operate within would help you develop a more accurate prioritization. Keeping in mind that which stage the company is at plays a significant role in its risk appetite, a smaller company still searching for product market fit may have a much higher risk appetite than a more mature company.
- Leveraging Cloud Services: Consider leveraging cloud services and outsourcing certain security functions to trusted providers. Cloud platforms often have built-in security controls that help reduce the burden on internal teams. It is important to note that this does not elevate the need for good security. All Cloud service providers follow a shared responsibility model where they do a lot of the heavy lifting but still depend on you to ensure best practices and secure configurations are followed.
- Automating Security Processes: Utilize security automation tools to streamline and automate security processes. Automation can help small teams manage their cybersecurity more efficiently and effectively.
- Employee Training and Awareness: Invest in regular training and awareness programs to educate employees about cybersecurity best practices. Employees are crucial in maintaining a secure environment and can be the first defense against cyber threats.
- Collaboration and Information Sharing: Collaborate with other SMBs, industry associations, and local cybersecurity communities. Sharing experiences, best practices, and threat intelligence can help smaller teams enhance their security posture.
Conclusion
Cybersecurity risk management is critical for organizations, especially SMBs, in an increasingly interconnected and threat-filled world; the threat is real. By following a well-defined risk management process, organizations can systematically identify, assess, and mitigate cyber risks, ensuring the protection of critical assets, infrastructure, and data. Although smaller teams may face resource constraints, adapting cybersecurity standards and best practices to meet their needs is possible. By prioritizing, leveraging cloud services, automating processes, investing in employee training, and fostering collaboration, SMBs can enhance their cybersecurity posture and effectively manage cyber risks.
Bonus 🎁 – Cyber Risk Mind Map
Cyber Risk Mind Map V1 is a complete mind map to help you brainstorm possible threats your business may face. The mind map underwent several iterations to ensure its comprehensive. Nothing is 100% complete, especially with the continuously changing cyber risks and your unique business environment, but it’s a great place to help broaden your horizon for risk assessments.
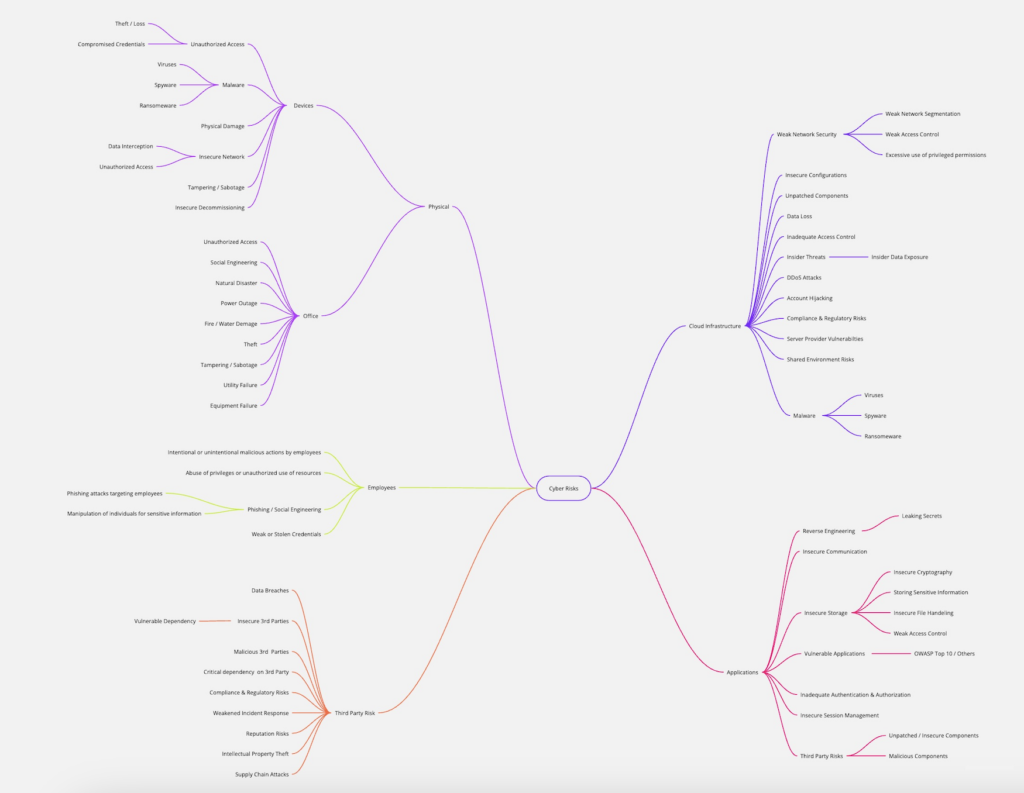
Sign up for my Newsletter below for a high-definition version of the Cyber Risk Mind Map. Also, to be the first to know about all new free content and resources as soon as they are out. 👇🏼